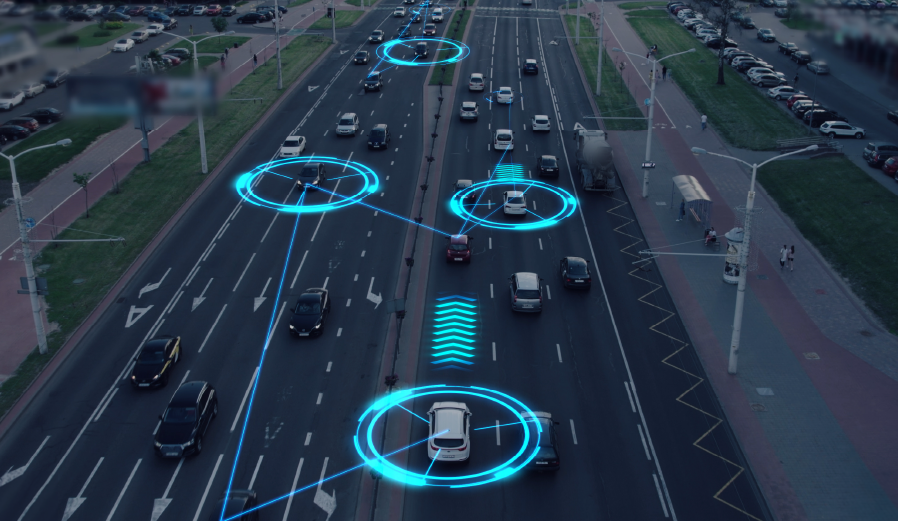
최근 우리 주변에서 자율주행 로봇을 마주치는 일이 점점 더 흔해지고 있습니다. 이는 인공지능이 새로운 국면으로 접어들고 있음을 보여주는 신호입니다. 엔비디아의 CEO 젠슨 황은 이러한 현상을 ‘피지컬 AI(Physical AI)’라 정의하며, "로봇의 챗GPT 모멘트가 오고 있다"고 선언했습니다. 피지컬 AI는 텍스트·이미지 생성 중심의 기존 AI를 넘어, 현실 세계에서 인식·추론·계획·행동을 수행하는 인공지능을 의미합니다. 문제는 이 변화 속도에 비해 보안과 신뢰 체계는 아직 준비되지 않았다는 점입니다. 우리는 기존 사이버 보안 규칙만으로는 대응할 수 없는 물리적 사고와 안전 위협의 시대로 들어서고 있습니다. 1. 피지컬 AI란 무엇인가: AI는 이제 ‘행동’한다 피지컬 AI(Physical AI)는 단순히 판단하는 AI가 아니라, 현실 공간에서 직접 움직이고 상호작용하는 AI입니다. 젠슨 황은 이를 “처리(Compute)–추론(Reasoning)–계획(Planning)–행동(Action)이 가능한 물리 AI”라고 설명합니다. 기존 AI가 디지털 세계에 머물렀다면, 피지컬 AI는 로봇이라는 물리적 매개체를 통해 도시, 공장, 물류 현장, 일상 공간으로 확장되고 있습니다. 다시 말해, 가상 세계의 AI가 현실 세계로 ‘나온 것’입니다. 2. 진짜 위험은 로봇이 아니라, 믿을 수 없는 세상이다 피지컬 AI 시대의 로봇은 단독으로 움이지 않습니다. 주변 인프라, 사람, 다른 로봇, 서비스, 시스템 등 모든것과 끊임없이 소통하며 움직여야 합니다. 이를 설명하는 개념이 바로 'R2X(Robot-to-Everything)'입니다. R2X는 단순히 로봇과 사물이 통신하는 기술을 넘어, 로봇이 "누구의 신호를 인식하고, 무엇을 믿고, 어떻게 행동할지" 결정하는 '상호작용 구조'를 의미합니다. '모든 것(Everything)'의 복잡성은 R2X를 구성하는 5가지 요소를 통해 명확해집니다. R2I (Robot-to-Infrastructure): 신호등, 출입문, 엘리베이터 같은 도시 인프라와의 상호작용 R2R (Robot-to-Robot): 다른 로봇과의 군집 행동이나 협력 R2H (Robot-to-Human): 사람의 음성, 제스처, 명령에 대한 반응 R2S (Robot-to-Service): 관제, 결제 등 클라우드 서비스와의 통신 R2E (Robot-to-Environment): 표지판, 시각 패턴 등 주변 환경 정보 인식 기존의 차량 통신 기술인 V2X와 비교하면 R2X가 마주한 도전의 크기를 짐작할 수 있습니다. 구분V2X (Vehicle-to-Everything)R2X (Robot-to-Everything)주체차량로봇(배송, 산업, 서비스)환경도로 중심, 규제된 공간보행로, 건물, 실내외상호 작용 대상차량, 신호등, 도로 인프라인프라, 로봇, 사람, 서비스행동 영향주행 제어이동/정지/접근/조작/인도위협 모델정형화되어 있음비정형화되어 있음 핵심적인 차이는 로봇이 마주하는 환경이 '비정형화'되어 있다는 점입니다. 도로나 신호 체계처럼 규칙이 명확한 공간과 달리, 로봇은 사전에 신뢰 관계가 없는 수많은 익명의 존재(사람, 다른 로봇, 임시 인프라 등)와 상호작용해야 합니다. 진짜 문제는 로봇 자체가 아니라, 로봇이 모든 것을 믿을 수 없는 복잡한 세상에서 작동해야 한다는 사실입니다. 3. 메시지 하나가 사고로 이어진다: R2X 보안의 핵심 위험 이처럼 혼란스러운 세상에서 위험이 침투하는 가장 주된 경로는 물리적 공격이 아닌 디지털 공격, 바로 '메시지' 그 자체입니다. 전통적인 IT 시스템에서 메시지는 데이터 처리 과정의 일부지만, R2X 환경에서 메시지는 곧 물리적인 행동으로 직결됩니다. 로봇은 출입문으로부터 '열림' 신호를 받으면 안으로 들어가고, '대기' 신호를 받으면 그 자리에 멈춥니다. 이러한 직접적인 연결은 메시지 조작이 곧 물리적 사고로 이어짐을 의미합니다. 예를 들어, 오염된 메시지는 다른 로봇으로부터 온 협력 신호를 위조해 의도적인 충돌을 유도(R2R 공격)하거나, 길바닥의 시각 패턴을 조작해 로봇이 제한 구역으로 들어가게 만들(R2E 공격) 수 있습니다. 즉, 잘못된 메시지 하나가 실제 사고를 만든다는 점이 피지컬 AI 보안의 본질입니다. 4. 기존의 보안 방식만으로는 충분하지 않다 이처럼 물리적 행동을 전제하는 R2X 환경에서는 기존 사이버 보안의 3대 원칙인 인증(Authentication), 인가(Authorization), 암호화(Encryption)만으로는 부족합니다. 물론, 공개 키 인프라(PKI)와 같은 강력한 기반 보안이 전제되어야 하는 것은 당연합니다. 하지만 그 위에 로봇이 수많은 신호 속에서 안전하게 판단하고 행동하기 위한 두 가지 새로운 보안 개념이 추가되어야 합니다. 상황 기반 신뢰 (Contextual Trust): 인증된 신호라 할지라도 현재 상황에 부합하는지 판단하는 능력입니다. 마치 열쇠(인증)가 있어 건물에 들어갈 권한이 있더라도, 화재 경보가 울리고 있다면 들어가지 않는 것이 상식인 것처럼, 로봇에게도 이런 디지털 '상식'이 필요합니다. 행동 일관성 검증 (Behavior Validation): 수신한 명령이 전체 임무와 모순되지 않는지 확인하는 '정신 점검'과 같습니다. 예를 들어, 101호에 택배를 배송하는 임무를 가진 로봇이 갑자기 옥상으로 가라는 명령을 받는다면, 행동 일관성 검증은 이를 비정상적이고 잠재적으로 위험한 지시로 판단하고 거부해야 합니다. 5. R2X 보안은 로봇의 '자격증'이 된다 결론적으로 R2X 보안은 로봇 기업이 선택적으로 추가할 수 있는 기술적 사양이 아닙니다. 이는 로봇이 도시에 진입하고 우리 일상에서 작동하기 위한 필수적인 전제 조건, 즉 '자격증'이 됩니다. 모빌리티 보안의 글로벌 플레이어 '새솔테크'는 이미 이 도전에 나서고 있습니다. 새솔테크 최근 산업통상자원부가 주관하는 도심 특화형 5G R2X(Robot to Everything) 기반 완전 자동화 라스트마일 배송 시스템 개발 및 실증' 사업의 보안 분야를 담당하며 현실 환경에서 R2X 보안을 구현하고 있습니다. 새솔테크 참여, R2X 기반 실증 사업 기사 자세히보기 이미 글로벌 완성차 업체(OEM)의 양산 차량에 V2X 보안 솔루션을 공급한 경험을 바탕으로, 미래의 위협인 양자 컴퓨터 공격에 대비한 양자내성암호(PQC) 기술까지 준비하며 R2X 보안을 선도하고 있습니다. 앞으로 R2X 보안 역량은 로봇 기업이 도시와 서비스 계약을 맺기 위한 핵심 '자격 조건'이 될 것입니다. 피지컬 AI시대, 신뢰할 수 있는 인프라가 곧 경쟁력 피지컬 AI 시대가 본격화되면서 로봇은 우리의 새로운 이웃이 되어가고 있습니다. 따라서 우리의 과제는 명확합니다. 로봇을 만드는 기술을 넘어, 로봇이 신뢰할 수 있는 세상을 설계하는 것입니다. 로봇이 우리 삶의 일부가 되는 미래, 우리는 그들이 안전하게 움직일 수 있는 디지털 신뢰 인프라를 구축할 준비가 되어 있을까요? 이 질문에 답하는 기업과 도시만이 피지컬 AI 시대의 주도권을 가져가게 될 것입니다.

피지컬 AI 시대의 도래, 우리가 진짜 걱정해야 할 5가지
2026년 01월 29일